Defences are implemented on the client, router, SD-WAN, cloud, and administrative layers.
Peplink technologies work together to generate a multi-layered defence against potential intrusions. To reach your network, attackers would need to defeat a battery of technologies, each defending a different part of the network from different forms of attack.

Defences are implemented on the client, router, SD-WAN, cloud, and administrative layers.
The client layer covers devices that end users interact directly with, as well as AP that delivers Wi-Fi to such devices.
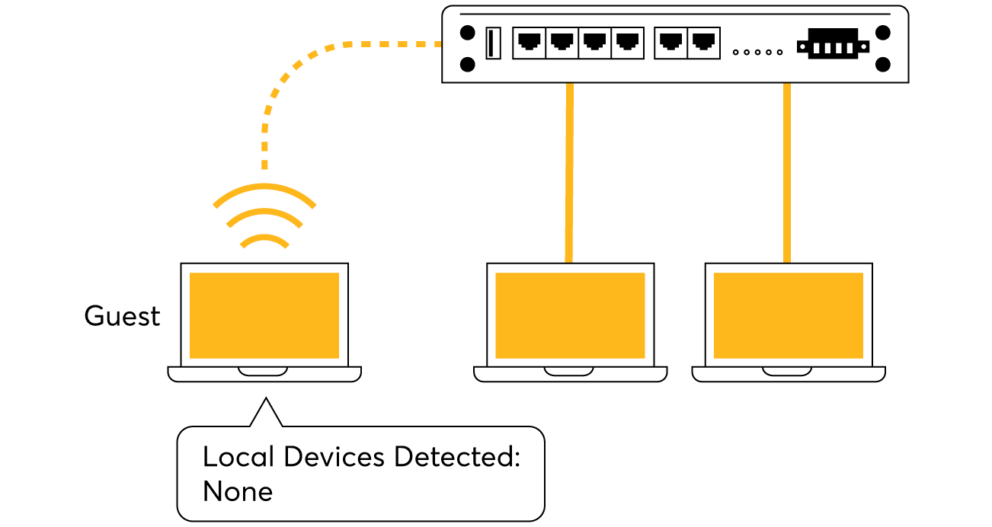
Create networks for guests to see only the internet with complete isolation from any other device connected to the router. Additionally any device on the guest network can't access the router's WebUI.
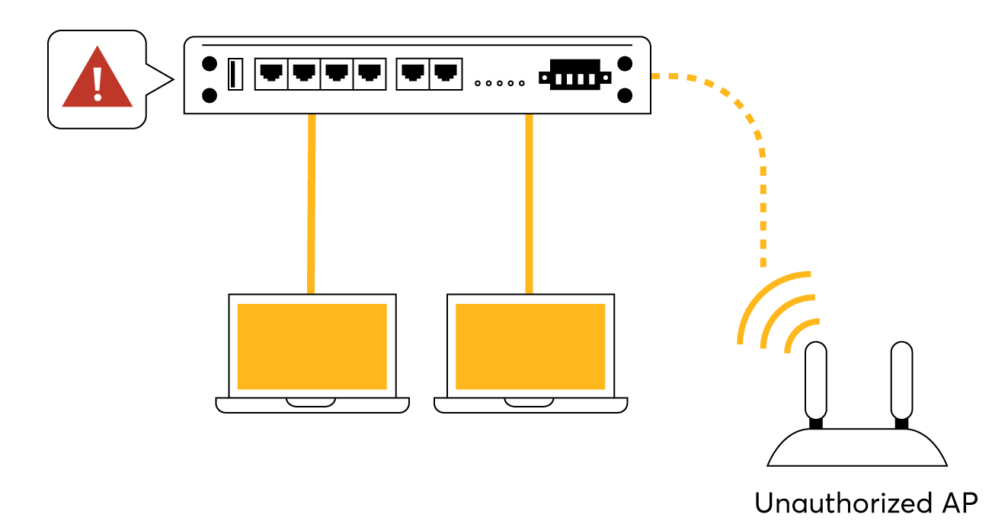
Identify any unauthorised AP connecting to your network.
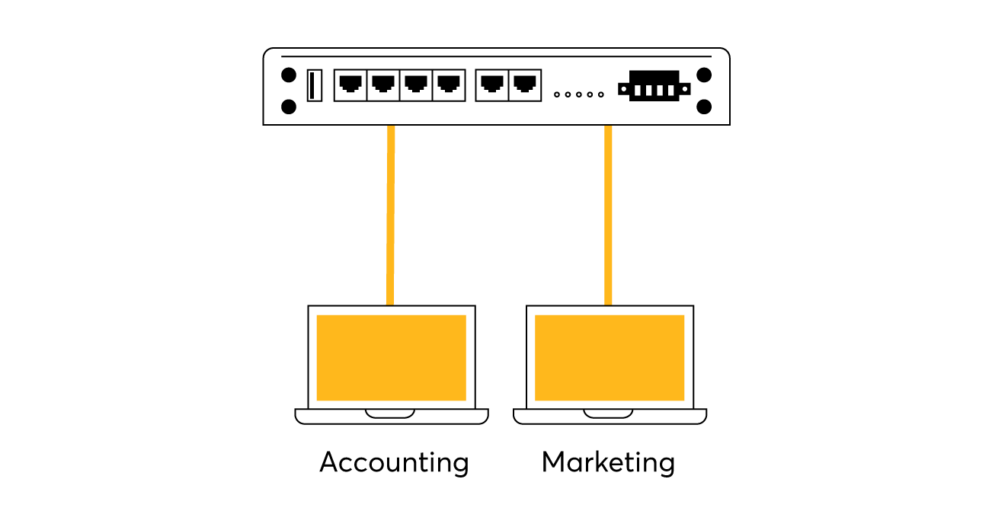
With InControl you can centralise your VLAN policies across all devices at multiple locations.
These features can also be virtualized on the cloud layer.
Having them both on the cloud and on the router makes it possible to secure local Internet breakout as well as VPN traffic.
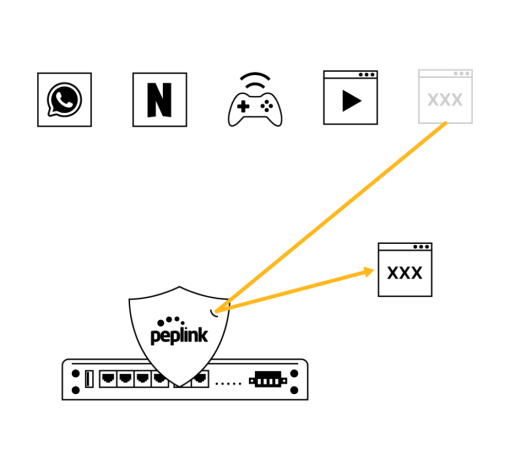
Each Peplink router has a dynamically updated web blocking tool that filters traffic into several categories. Users simply need to choose the categories they wish to block, and the router will take care of the rest.
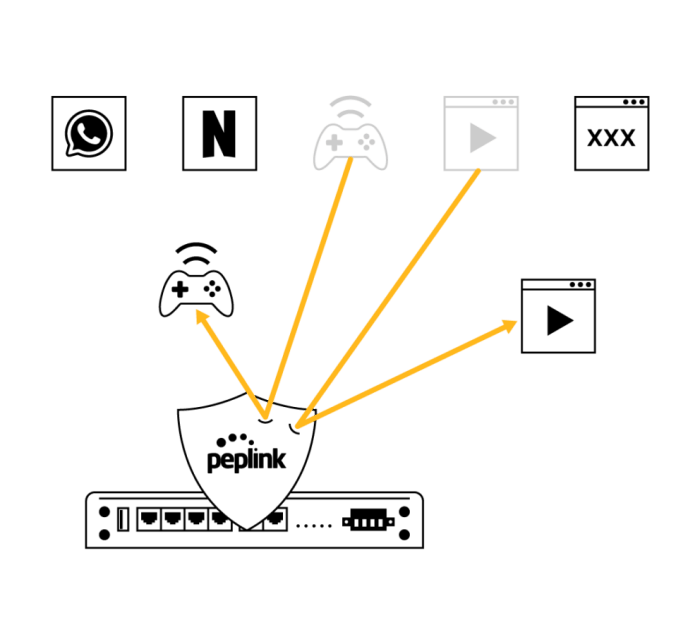
Outbound Policy and firewall rules are only effective if they are usable. With Peplink gear, you can set firewall rules based on application and even by country. With InControl, you can centralize firewall rules and outbound policy for multiple devices.
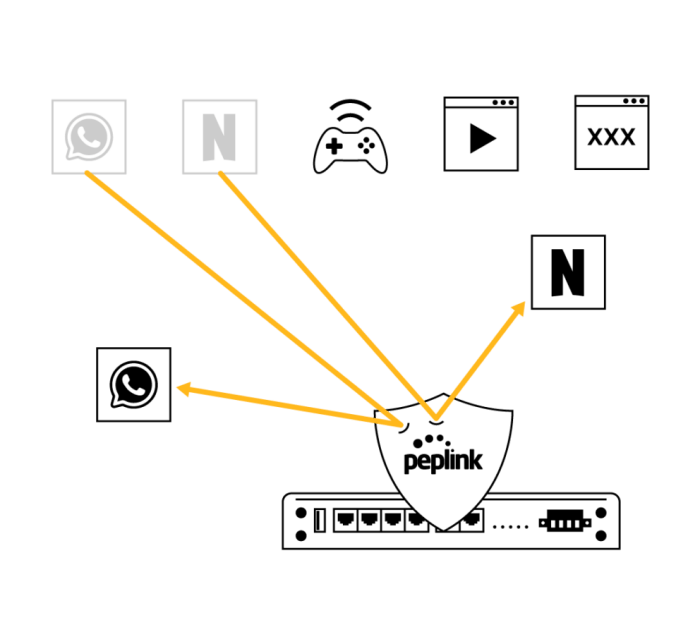
For applications that First Packet Inspection cannot recognise, there is Deep Packet Inspection. Block prevalent distractions such as streaming sites, social media platforms, and instant messengers.
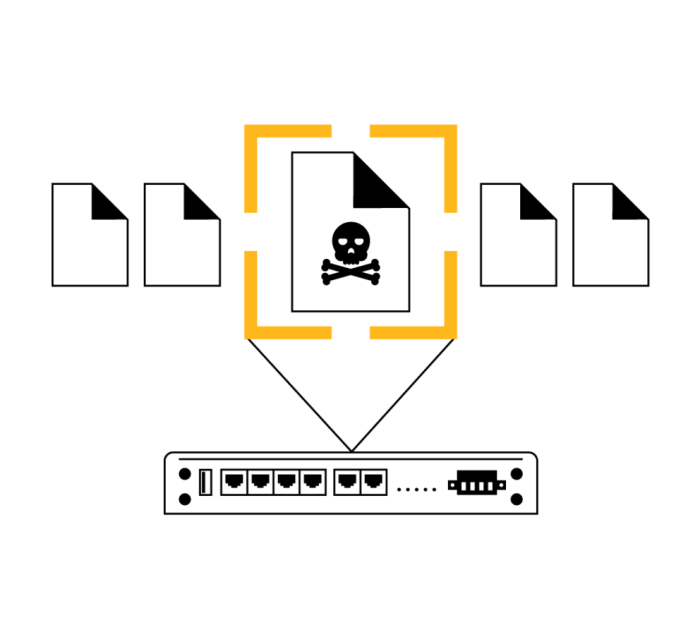
Each Peplink router has a built-in DoS protection feature. Once enabled, it can detect and block abnormal packets as well as suspicious traffic typical of intrusion and denial of service attacks.

There are always new threats and vulnerabilities to be discovered. When one emerges, Peplink will quickly develop and deploy new firmware to address the threats. We update firmware for our products years after they have been launched.
The SD-WAN layer covers the security of the data as it travels across WAN links.
Peplink’s patented SpeedFusion technology provides a significant advantage on this layer.
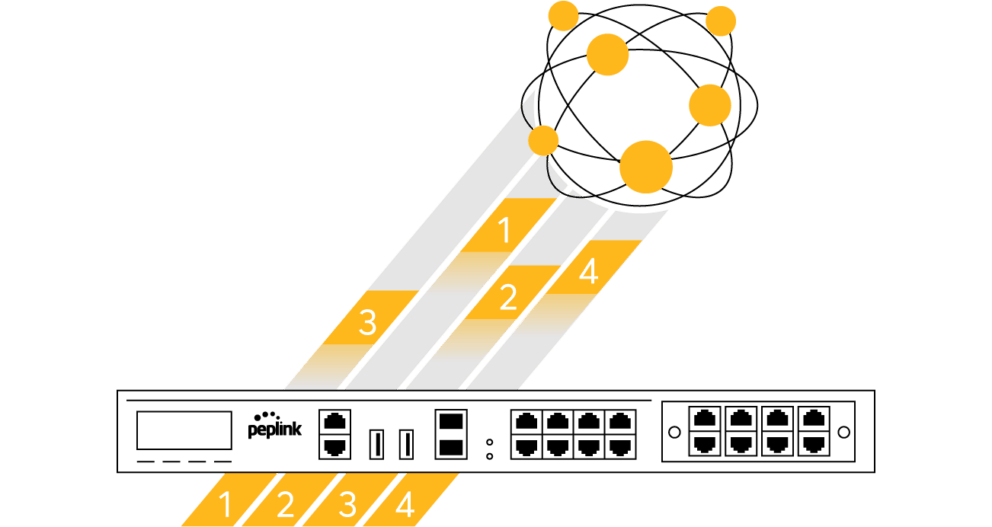
Once the SpeedFusion tunnel is formed, sessions are broken down to packets and sent separately across available WAN-to-WAN connections. Because each connection is encrypted separately, potential hackers would need to obtain the key to every connection

Each secure WAN-to-WAN link is established through a Diffie-Hellman key exchange. This produces randomly changing data encryption keys to protect data with a 256-bit AES cryptographic algorithm. 256-bit AES would take the world’s fastest supercomputer millions of years to crack.
FusionHub can be installed on cloud services for cloud-based security. Combined with a Peplink router, and you can secure both organizational VPN traffic as well as branch office Internet breakout.
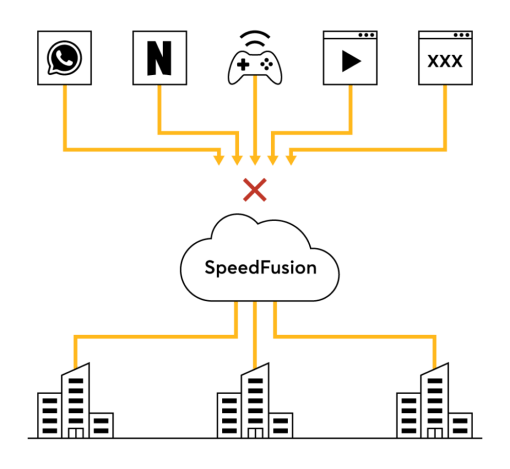
Use web blocking, firewall, outbound policy, DPI application filtering to control what type of traffic can access your network. Protect your entire network with Intrusion detection and DOS protection. Any security feature that our routers have can also be applied to the cloud.

Peplink's cloud appliance supports VRF, which divides the appliance into groups and holds a separate routing table for each group. The result: one cloud appliance can host several tenants, with each of them completely isolated from each other.
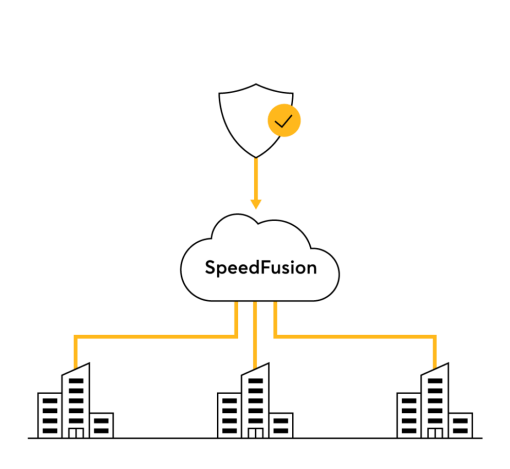
When vulnerabilities appear, Peplink swiftly develop patches and make them available to the users. These patches are available on Peplink's cloud services as well as their routers, securing your entire network.
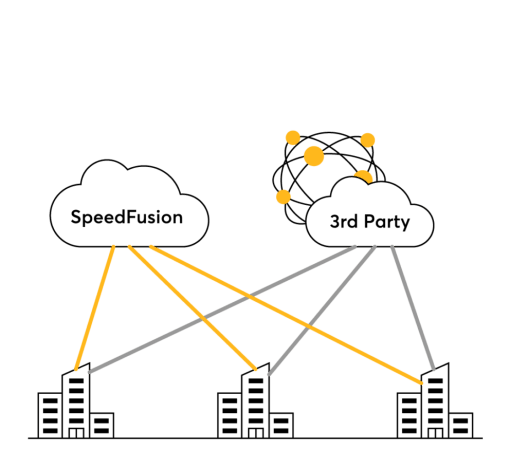
Works together with your 3rd-party cloud-based security solution. Secure organisation traffic with our security features, and secure public Internet traffic with the 3rd-party solution of your choice using IPsec or OpenVPN.
The human layer covers credentials carried by an organisation’s team members.
Countermeasures protect passwords and minimise the potential harm done by a breach.
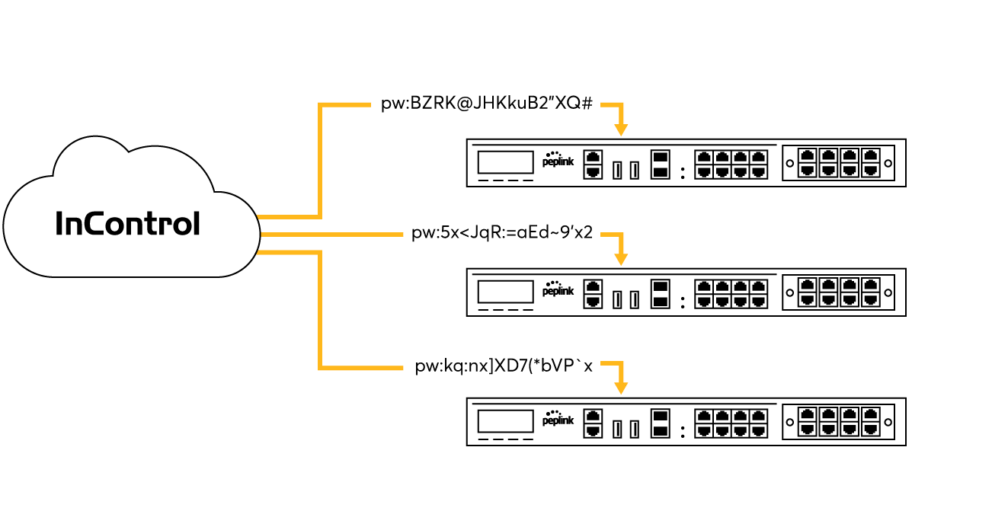
One of a router’s simplest attack vectors is the admin password. With InControl, you can change the admin password for multiple devices at the same time. Doing so at regular intervals will significantly increase the network’s level of security.
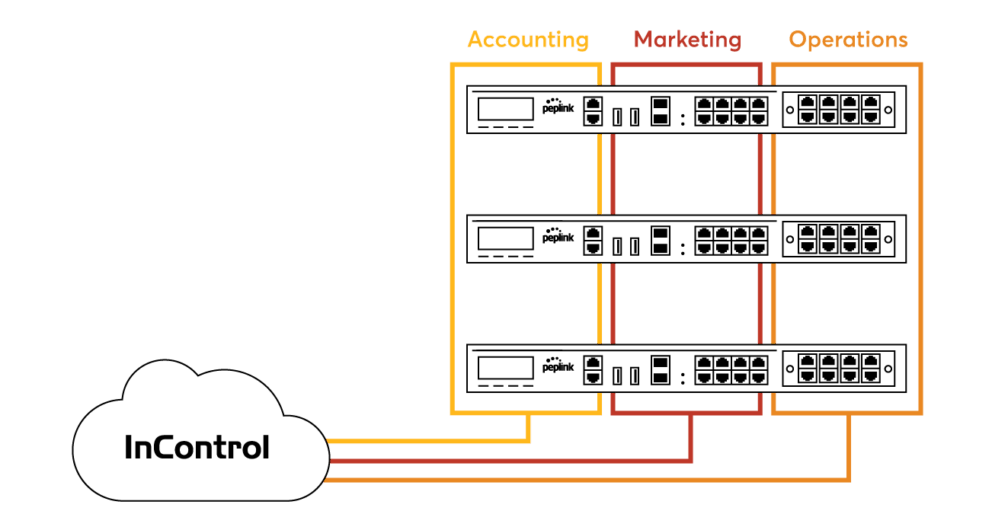
Separating your network into different trust boundaries will minimise the damage caused by a compromised credential. Use VLANs to separate the networks for different teams, each with separate login gateways. Use InControl to set up different access levels for each administrator.
Companies who are dealing with credit card and payment information must meet the requirements set by the Payment Card Industry Data Security Standards (PCI DSS).
Peplink routers are capable of meeting PCI DSS 3.2 requirements. We have prepared an easy-to-read compliance guide containing step-by-step instructions with UI screenshots each step of the way. With this guide, you will learn how to build and maintain your PCI DSS compliant network using Peplink routers.
This guide is applicable to Balance and MAX routers, running the latest firmware.
Document Version: 1.1
Published: July, 2017
Download the guide
Enterprises and government agencies demand the highest assurance that our cryptographic technology is certified to be secure: FIPS 140-2 is the answer.
Published by the U.S. National Institute of Standards and Technologies (NIST), the Federal Information Processing Standard (FIPS) is used by the U.S. government to approve cryptographic modules for encrypting network traffic.
This security standard is recognised by the U.S. and Canadian governments. It is also a source of confidence for banking and finance sectors, and large multinational enterprises.
FAQ Fact sheet
How can we help you today?
We are just a click away ...